Monitor & Alert on Inactive AWS IAM Users with Slack Notifications
Last edited 115 days ago
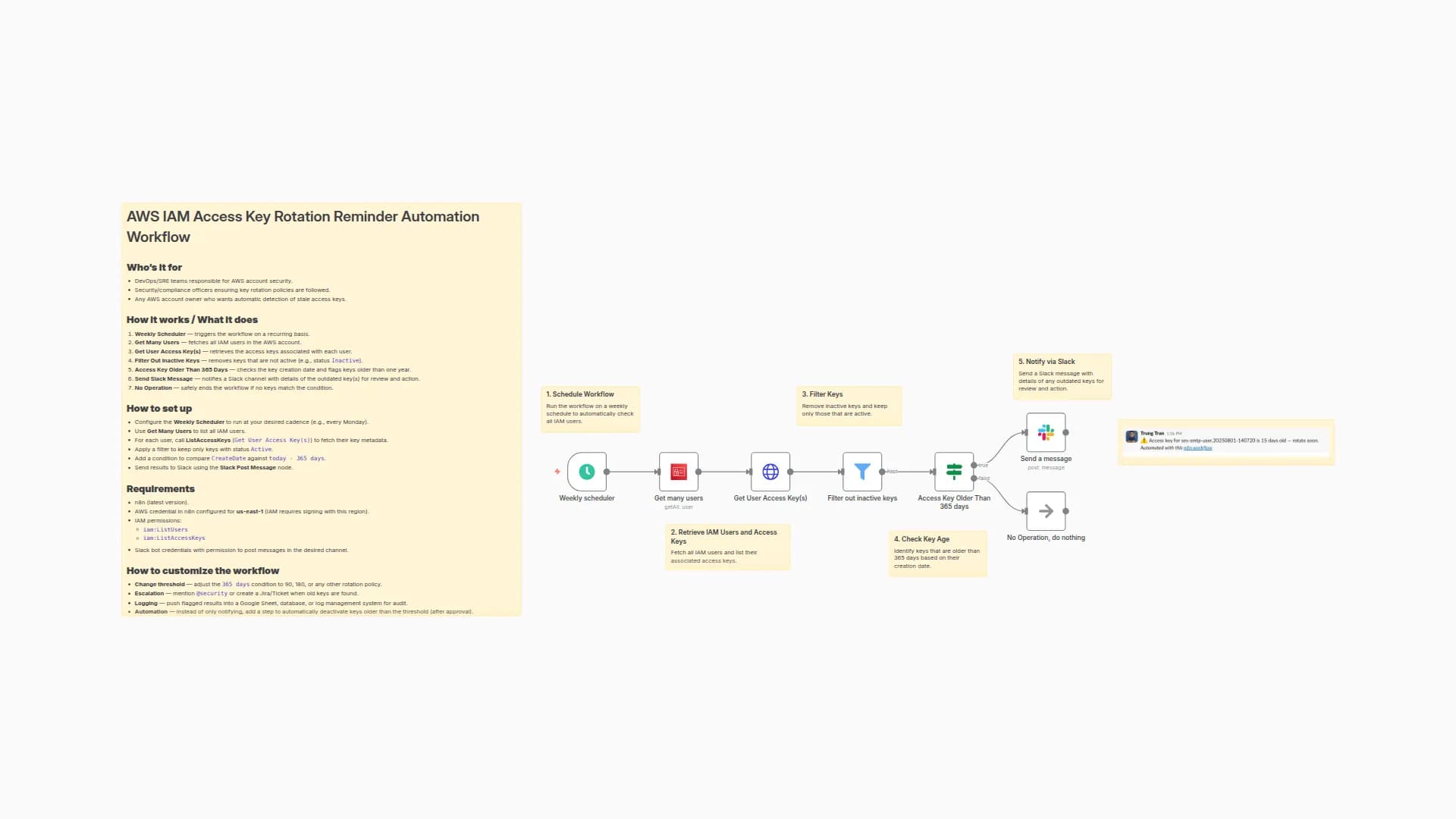
AWS IAM Inactive User Automation Alert Workflow
Weekly job that finds IAM users with no activity for > 90 days and notifies a Slack channel.
⚠️ Important: AWS SigV4 for IAM must be scoped tous-east-1. Create the AWS credential in n8n with region us-east-1 (even if your other services run elsewhere).
Who’s it for
- SRE/DevOps teams that want automated IAM hygiene checks.
- Security/compliance owners who need regular inactivity reports.
- MSPs managing multiple AWS accounts who need lightweight alerting.
How it works / What it does
- Weekly scheduler – kicks off the workflow (e.g., every Monday 09:00).
- Get many users – lists IAM users.
- Get user – enriches each user with details (password status, MFA, etc.).
- Filter bad data – drops service-linked users or items without usable dates.
- IAM user inactive for more than 90 days? – keeps users whose last activity is older than 90 days.
- Last activity is derived from any of:
PasswordLastUsed(console sign-in)AccessKeyLastUsed.LastUsedDate(fromGetAccessKeyLastUsedif you add it)- Fallback to
CreateDateif no usage data exists (optional)
- Last activity is derived from any of:
- Send a message (Slack) – posts an alert for each inactive user.
- No operation – path for users that don’t match (do nothing).
How to set up
- Credentials
- AWS (Predefined → AWS)
- Service:
iam - Region:
us-east-1← required for IAM - Access/Secret (or Assume Role) with read-only IAM perms (see below).
- Service:
- Slack OAuth (bot in your target channel).
- AWS (Predefined → AWS)
Requirements
- n8n (current version).
- AWS IAM permissions (minimum):
iam:ListUsers,iam:GetUser- (Optional for higher fidelity)
iam:ListAccessKeys,iam:GetAccessKeyLastUsed
- Slack bot with permission to post in the target channel.
- Network egress to
iam.amazonaws.com.
How to customize the workflow
- Change window: set 60/120/180 days by adjusting
minus(N, 'days'). - Audit log: append results to Google Sheets/DB with
UserName,Arn,LastActivity,CheckedAt. - Escalation: if a user remains inactive for another cycle, mention
@securityor open a ticket. - Auto-remediation (advanced): on a separate approval path, disable access keys or detach policies.
- Multi-account / multi-region: iterate a list of AWS credentials (one per account; IAM stays
us-east-1). - Exclude list: add a static list or tag-based filter to skip known service users.
Notes & gotchas
- Many users never sign in; if you don’t pull
GetAccessKeyLastUsed, they may look “inactive”. Add that call for accuracy. PasswordLastUsedis null if console login never happened.- IAM returns timestamps in ISO or epoch—use
toDate/toDateTimebefore comparisons.
You may also like
New to n8n?
Need help building new n8n workflows? Process automation for you or your company will save you time and money, and it's completely free!