Send Slack Alerts for AWS IAM Access Keys Older Than 365 Days
Last edited 115 days ago
AWS IAM Access Key Rotation Reminder Automation Workflow
Watch the demo video below:
Who’s it for
- DevOps/SRE teams responsible for AWS account security.
- Security/compliance officers ensuring key rotation policies are followed.
- Any AWS account owner who wants automatic detection of stale access keys.
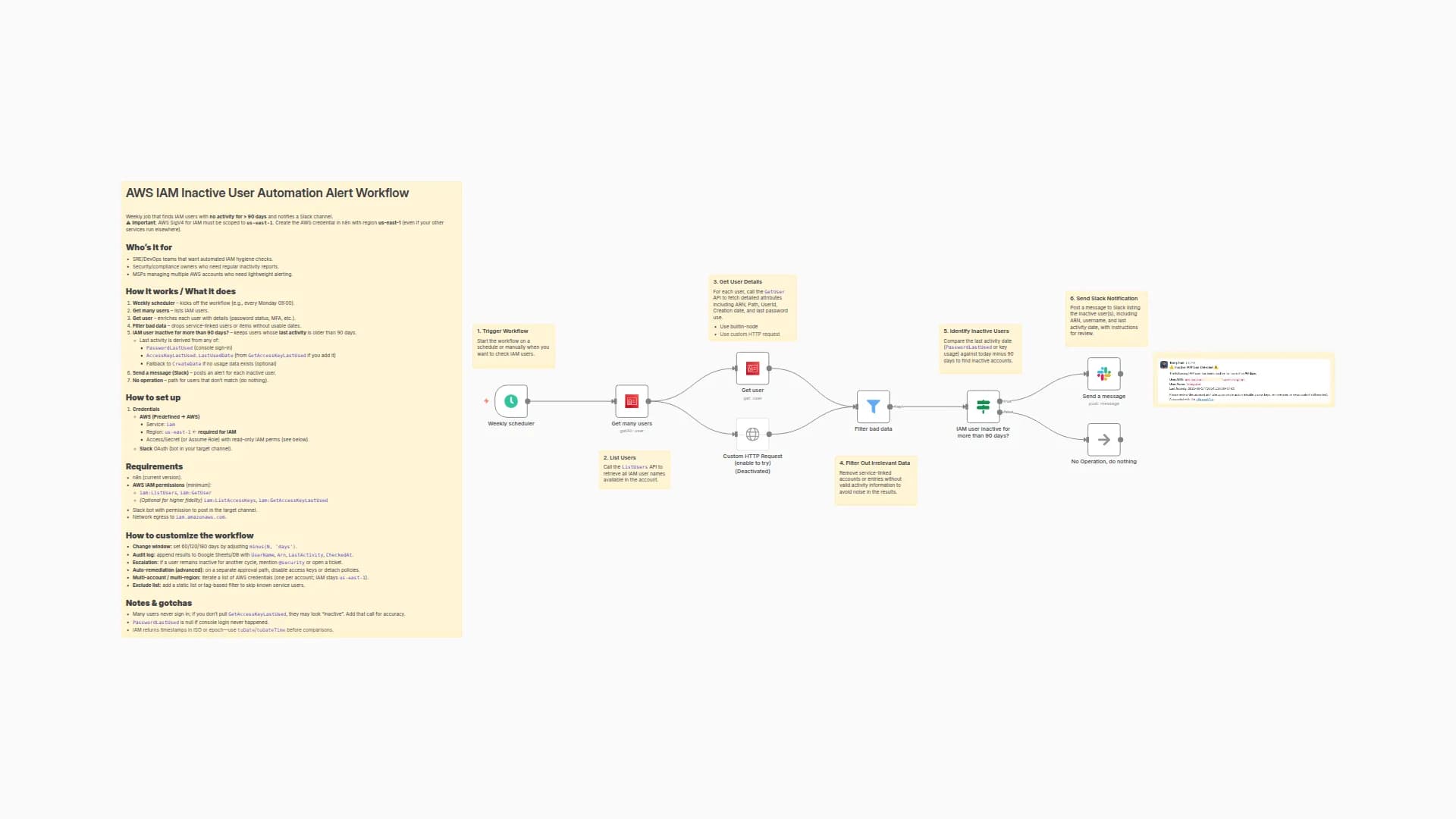
How it works / What it does
- Weekly Scheduler — triggers the workflow on a recurring basis.
- Get Many Users — fetches all IAM users in the AWS account.
- Get User Access Key(s) — retrieves the access keys associated with each user.
- Filter Out Inactive Keys — removes keys that are not active (e.g., status
Inactive). - Access Key Older Than 365 Days — checks the key creation date and flags keys older than one year.
- Send Slack Message — notifies a Slack channel with details of the outdated key(s) for review and action.
- No Operation — safely ends the workflow if no keys match the condition.
How to set up
- Configure the Weekly Scheduler to run at your desired cadence (e.g., every Monday).
- Use Get Many Users to list all IAM users.
- For each user, call ListAccessKeys (
Get User Access Key(s)) to fetch their key metadata. - Apply a filter to keep only keys with status
Active. - Add a condition to compare
CreateDateagainsttoday - 365 days. - Send results to Slack using the Slack Post Message node.
Requirements
- n8n (latest version).
- AWS credential in n8n configured for us-east-1 (IAM requires signing with this region).
- IAM permissions:
iam:ListUsersiam:ListAccessKeys
- Slack bot credentials with permission to post messages in the desired channel.
How to customize the workflow
- Change threshold — adjust the
365 dayscondition to 90, 180, or any other rotation policy. - Escalation — mention
@securityor create a Jira/Ticket when old keys are found. - Logging — push flagged results into a Google Sheet, database, or log management system for audit.
- Automation — instead of only notifying, add a step to automatically deactivate keys older than the threshold (after approval).
- Multi-account support — duplicate or loop across multiple AWS credentials if you manage several AWS accounts.
You may also like
New to n8n?
Need help building new n8n workflows? Process automation for you or your company will save you time and money, and it's completely free!